Friday, December 19, 2008
Source code auditing tool
Seeker Developer By Sunjester:
Seeker is a source code auditing tool capable of locating and finding bugs in any source code provided you have the right scanstring. seeker is developed in c# and utilizes the .NET framework.
Download Link:
http://devsun.info/projects/dbc/release.rar
Seeker is a source code auditing tool capable of locating and finding bugs in any source code provided you have the right scanstring. seeker is developed in c# and utilizes the .NET framework.
Download Link:
http://devsun.info/projects/dbc/release.rar
Wikto 2.1.0.0 (xmas Edition) Released
Wikto is a tool that checks for flaws in webservers. It provides much the same functionality as Nikto but adds various interesting pieces of functionality, such as a Back-End miner and close Google integration

Changelog
Fixed incorrect links spider bug
Added time anomaly functionality in backend scanner
Added easy access (and icons) to findings in backend scanner
Fixed .exe finding occasionally not showing bug
Click here to Download

Changelog
Fixed incorrect links spider bug
Added time anomaly functionality in backend scanner
Added easy access (and icons) to findings in backend scanner
Fixed .exe finding occasionally not showing bug
Click here to Download
Saturday, December 13, 2008
I Breath/ I Drunk
The latest weapon to tackle drunk driving has been unleashed in the United States,so it wont be logn before this useful gadget reaches our shores. Hail iBreath, a nifty little accesory that allows users and pub crawlers alike to check their blood alcohol content and see if they need to hail a cab to drive them home
The funky breathanalyser is the first device of its kind to be compatible with the ipod as well as the iphone.In India thought,the company service center doesn't have the foggiest idea of a launch date yet.
The device can measure an individual's blood alcohol range within 0.000-0.100 per cent, and can remind users when its time for their next breath test.
The iBreath has just gone on sale in Britain,and promises to give users an accurate reading of how much has been knocked back.The gadget clips on to the base of an iPod and has a fold-out tube to blow into.It workds in much the same way as a police breathanalyser does.The Unit which rather bizarrely also includes an FM radio, has been a pre-christmas hit in the US and is being touted as "the Ultimate IPod accessory". As a retalier says"Not only can this cool gizmo save you from career-ending embarassment,It can potentially save you a lot of money in legal fees and jail time".
Lets Drink to that
The funky breathanalyser is the first device of its kind to be compatible with the ipod as well as the iphone.In India thought,the company service center doesn't have the foggiest idea of a launch date yet.
The device can measure an individual's blood alcohol range within 0.000-0.100 per cent, and can remind users when its time for their next breath test.
The iBreath has just gone on sale in Britain,and promises to give users an accurate reading of how much has been knocked back.The gadget clips on to the base of an iPod and has a fold-out tube to blow into.It workds in much the same way as a police breathanalyser does.The Unit which rather bizarrely also includes an FM radio, has been a pre-christmas hit in the US and is being touted as "the Ultimate IPod accessory". As a retalier says"Not only can this cool gizmo save you from career-ending embarassment,It can potentially save you a lot of money in legal fees and jail time".
Lets Drink to that
Sunday, December 7, 2008
Password protect your messages with SMS guard

Many times we don’t want others to read our private messages but also don’t want to delete them. And there is no security setting in any nokia mobile to password protect messages.
Here is an app which will help you to keep your messages password protected.
You can download sms guard from link given below.
Click here to download
Install this software in your nokia s60 v2 mobile and open it.
At first it will ask for password to set. Enter the password and next time it will ask for the password to login.Log in using the password you set . Now you’ll be able to see all your inbox messages in this software. Now select the message you want to lock , click on options and select ‘Lock Message’.
Now nobody can see your private messages without your permission.
This software works with all symbian s60 v2 mobile phones ,N-gage QD and some n series phones.
e.g 6600, 3230, n70, n72, 7610, 6630, 6670
Get Gmail On Your Desktop
Google recently developed a Google Desktop Gadget known as Gmail Gadget. Just log into your account and this gadget will fetch your mails in your desktop. You can easily mail, send replies, from your desktop with this gadget. This is the fastest method to search Gmail !
Download Instructions :Click here to Download

Download Instructions :Click here to Download
Thursday, November 20, 2008
Etherpad-Better than GoogleDocs ?
Just came to know about a new tool launched by Appjet known as Etherpad well definately its a revolution and something new some may argue that there are other similar tools like SubEthaEdit but its for MAC and its paid Etherpad is free maybe not so reliable but it does offer something new if many people want to simultaneously want to edit many things
You can try yourself Etherpad at
http://etherpad.com/
You can try yourself Etherpad at
http://etherpad.com/
Monday, November 17, 2008
Prevent Virus Spreading From USB Flash Drives With iKill
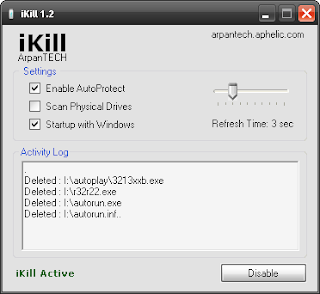
Here is a simple tool known as iKill which prevents the spreading of viruses from Pen Drive to your PC.
It works by scanning the drives for the presence of removable drives. If found, it parses the autorun.inf file for the executables it may run. If AutoProtect is enabled,it will automatically delete the files present on the drive. Otherwise, it will prompt you for your permission to delete the virus. Version 2 includes unspecified updates.
Download
Saturday, November 15, 2008
Save youtube videos directly from Firefox3 cache
Open the youtube video page in firefox 3. Allow the video to play once.
Now the video is finished playing. Open a new tab in firefox 3. In the location bar (address bar) type
about:cache
and press enter. A new page will load. In the page see the heading
Disk cache device
Under that there is “Cache Directory”. There will be a long address similar to one shown below
C:\Documents and Settings\usrname\Local Settings\Application Data\Mozilla\Firefox\Profiles\abcd123h.default\Cache
Copy the full address (You must copy the cache link address from your computer. The above address is just to show and make you understand). Now open “My Computer”. In the address bar paste the already copied long address.
A folder will open. This folder contains the youtube video file in the form of cache. Note that the video file will be big in size. Now open VLC Media player or any other flv player. Drag and drop the bigger cache file in the media player. The file that plays the video is your video file. Copy and paste it in desktop. Rename the file to yourvideo1.flv (or any other name of your choice with flv extension).
Now you have saved the youtube video right from your firefox 3 cache rather than downloading it again.
You can watch the saved video while offline.
Tested in WinXP, Firefox3
Now the video is finished playing. Open a new tab in firefox 3. In the location bar (address bar) type
about:cache
and press enter. A new page will load. In the page see the heading
Disk cache device
Under that there is “Cache Directory”. There will be a long address similar to one shown below
C:\Documents and Settings\usrname\Local Settings\Application Data\Mozilla\Firefox\Profiles\abcd123h.default\Cache
Copy the full address (You must copy the cache link address from your computer. The above address is just to show and make you understand). Now open “My Computer”. In the address bar paste the already copied long address.
A folder will open. This folder contains the youtube video file in the form of cache. Note that the video file will be big in size. Now open VLC Media player or any other flv player. Drag and drop the bigger cache file in the media player. The file that plays the video is your video file. Copy and paste it in desktop. Rename the file to yourvideo1.flv (or any other name of your choice with flv extension).
Now you have saved the youtube video right from your firefox 3 cache rather than downloading it again.
You can watch the saved video while offline.
Tested in WinXP, Firefox3
Saturday, September 13, 2008
Google Chrome Easter Egg Revealed
Just type about:internets on the Google chrome address bar, you will find images of animated colorful tubes.

These tubes are known as “Series of Tubes”
“Series of tubes” is an analogy used by U.S Senator Ted Stevens to describe the Internet in the context of Network Neutrality.
You can also try:
about:version
about:memory
about:stats
about:network
about:dns
about:cache
about:histograms
about:plugins

These tubes are known as “Series of Tubes”
“Series of tubes” is an analogy used by U.S Senator Ted Stevens to describe the Internet in the context of Network Neutrality.
You can also try:
about:version
about:memory
about:stats
about:network
about:dns
about:cache
about:histograms
about:plugins
Tuesday, September 2, 2008
How to hide your Java code to prevent from being decompiled
Decompilation is the process of turning object code into source code. This should make sense, since compilation is the process of turning source code into object code. But what is object code? Roughly defined, object code is code expressed in a language that is executed directly by a real or virtual machine. For languages like C, the object code is generally run on a hardware CPU, while Java object code generally runs on a virtual machine.
As described above, decompilation may sound fairly simple, but it's actually quite hard -- it essentially involves inferring large-scale, high-level behavior from small-scale, low-level behavior. To understand this intuitively, think of a computer program as a complex corporate structure. High-level managers dispense commands such as "maximize technology throughput" to their underlings, who then turn these commands into more concrete actions, such as installing the new XML database.
As a new employee at this corporation, you might ask an underling what he or she was doing, and get the response, "I'm installing a new XML database." From that statement, you wouldn't be able to infer that the final goal was to maximize technology throughput. After all, the ultimate goal could be something quite different, such as discretizing the supply chain structure or aggregating consumer data.
But if you were the curious type, you might ask a few more questions, and you might spread your questions around, asking several underlings at different levels of the company. Eventually, you could put all the answers together and you might be able to guess that the larger corporate goal was to maximize technology throughput.
If you think of a computer program working like a corporate structure, then the above analogy should give you an intuitive sense of why decompiling code isn't trivial. For a more theoretical perspective, here's how Cristina Cifuentes, a leading researcher in the area, describes the process of decompilation:
Any binary reengineering project requires the disassembly of the code stored in the binary file. From a theoretical point of view, the separation of data and code in von Neumann machines is equivalent to the halting problem; hence, a complete static translation is not possible. However, in practice, different techniques can be used to increase the percentage of code that is translated statically, or hooks to dynamic translation techniques can be used at run-time.
--"Binary Reengineering of Distributed Object Technology"
Turning object code into source code isn't the only issue at hand when it comes to decompilation. A Java class file potentially contains a number of different kinds of information. Knowing what kind of information a class file might contain is important to understanding what you can do with, and to, that information. And that's where a Java disassembler comes in.
The actual binary format of the Java class file isn't important. What is important is knowing what different pieces of information are contained in those bytes. To this end, we'll employ a tool that comes with most JDKs -- javap. javap is a Java code disassembler, which is not the same as a decompiler. A disassembler turns object code that is in a machine-readable format (as shown in Listing 1) into something human-readable (as shown in Listing 2).
0000000 feca beba 0300 2d00 4200 0008 081f 3400
0000020 0008 073f 2c00 0007 0735 3600 0007 0737
0000040 3800 0007 0a39 0400 1500 000a 0007 0a15
0000060 0800 1600 000a 0008 0a17 0800 1800 0009
...
Output of javapLocal variables for method void priv(int)
Foo this pc=0, length=35, slot=0
int argument pc=0, length=35, slot=1
Method void main(java.lang.String[])
0 new #4
3 invokespecial #10
6 return
Note that the output shown in Listing 2 isn't quite source code. The first half of the listing is a list of local variables for a method; the second half is assembly code, which is human-readable object code.
javap is used to disassemble, or unpack, a class file. Here's a quick run-down of the information contained in a Java class file, which can be disassembled using javap:
Member variables. Every class file contains all the naming and typing information for each data member of its class.
Disassembled methods. Each method of the class is represented, along with its type signature, by a string of virtual machines instructions.
Line number. Each section of each method is mapped to the source code line that it was generated from (when possible). This provides the run-time system, and debuggers, the ability to provide a stack trace for a running program.
Local variable names. The variables local to a method don't really need names once the methods are compiled, but they can be included using the -g option to the javac compiler. These, too, help the run-time system and the debugger to help you.
Now that we know a little bit about what's going on inside a Java class file, let's take a look as how we can tweak this information to our own ends.
Conceptually, using a decompiler is easy. It's the inverse of a compiler: you give it a .class file, and it gives you a source code file.
Some of the newer decompilers have intricate graphical interfaces, but we'll use Mocha, which was the first publicly available decompiler, for our initial examples. At the end of this article, I'll discuss JODE, one of the newer decompilers available under the GPL. (See Resources to download Mocha and for a list of Java decompilers.)
Let's say you have a class file called Foo.class sitting in your directory. Decompiling it with Mocha is as easy as typing the following command:
$ java mocha.Decompiler Foo.class
This produces a new file, called Foo.mocha (Mocha applies the name Foo.mocha to avoid overwriting any source code in the original file). The new file is a Java source file, and assuming all went well you can now compile it normally. Just rename it to Foo.java and go.
But there's a hitch: if you run Mocha on some code you have lying around, you may notice that the code it generates isn't identical to the source. I'll run an example so that you can see what I mean. The original source shown in Listing 3 is from a test program called Foo.java.
private int member = 10;
public Foo() {
int local = returnInteger();
System.out.println( "foo constructor" );
priv( local );
}
And here's the code generated by Mocha.
private int member;
public Foo()
{
member = 10;
int local = returnInteger();
System.out.println("foo constructor");
priv(local);
}
The two snippets differ in where the member variable member is initialized to 10. In the original source, it's expressed as an initial value on the same line as the declaration; in the decompiled source, it's expressed as an assignment statement inside the constructor. The decompiled code tells us something about the way the original source was compiled; namely that its initial values were compiled as assignments in the constructor. You can learn a lot about the way Java compilers work by looking at decompilations of their output.
As valiantly as Mocha works to decompile your object code, it doesn't always succeed. No decompiler is able to render the source with complete accuracy, due to the difficulty of the problem, and every decompiler handles the holes in its rendering differently. For example, Mocha sometimes has trouble figuring out the exact structure of looping constructs. When this happens, it resorts to using fake goto statements in the resulting output, as shown in Listing 5.
if (i1 == i3) goto 214 else 138;
j3 = getSegment(i3).getZOrder();
if (j1 != 1) goto 177 else 154;
if (j3 > k2 && (!k1 || j3 <> j2)) goto 203 else 196;
expression 0
if == goto 201
continue;
Code obfuscation is literally the act of obscuring your code. A Java obfuscator changes a program in subtle ways, such that it behaves identically as far as the JVM is concerned, but is more confusing to the human trying to understand it.
Let's look at a sample of what happens when a decompiler runs up against obfuscated code. Listing 6 shows the result of Mocha's attempt to decompile Java code that had been obfuscated by a tool called jmangle. Note that the snip below is the same one we've used in the previous listings, though you certainly wouldn't think so at first glance.
public Foo()
{
jm2 = 10;
int i = jm0();
System.out.println("foo constructor");
jm1(i);
}
An obfuscator such as jmangle changes many of the variable and method names (and sometimes even class and package names) into meaningless strings. This results in a program that is difficult for humans to read, but which is essentially the same as the original as far as the JVM is concerned.
All obfuscators make symbols meaningless, but that's not all they do. Crema was notorious for the many nasty ways it could foil decompilation, and many of the obfuscators that have been created since then have followed its lead.
One popular way to obscure source is to take the meaningless-string trick to the next level, by replacing a symbol from the class file with an illegal string. The replacement might be a keyword like private, or, even worse, a completely meaningless symbol such as ***. Some virtual machines -- especially in browsers -- don't take kindly to such antics. Technically, a variable such as = is contrary to the Java specification; some virtual machines will overlook it, others will not.
Another one of Crema's tricks was, literally, the bomb. Crema was armed with the ability to completely shut Mocha down. It did so by adding a little "bomb" to the compiled code, which caused Mocha to crash when it attempted to decompile the code.
Sadly, Crema is no longer available, but a tool called HoseMocha, like Crema, was designed specifically to shut Mocha down. To see how HoseMocha works, we'll use our trusty disassembler, javap. Listing 7 shows the code before HoseMocha has planted its bomb.
Method void main(java.lang.String[])
0 new #4
3 invokespecial #10
6 return
And here's the code after HoseMocha has had its way with it.
Method void main(java.lang.String[])
0 new #4
3 invokespecial #10
6 return
7 pop
Do you see the bomb? Note that the routine now has a pop instruction after the return. But wait -- how can a function do something after it's returned? Obviously, it can't, and that's the trick. Placing an instruction after a return statement ensures that it will never be executed. What you see here is essentially impossible to decompile. It doesn't make any sense because it doesn't correspond to any possible Java source code.
But why does this little glitch cause Mocha to crash? It could just as easily ignore it, or send a warning and move on. While Mocha's vulnerability to this type of bomb could be considered a bug, it's more likely that it was deliberately created by van Vliet in response to all the concern about Mocha.
So far, we've looked at older decompilation and obfuscation tools -- oldies but goodies. But such tools have become increasingly sophisticated over the years, particularly with regard to graphical interface. We'll close with a look at one of the newer decompilers, just to give you an idea of what's out there.
i2 = i3;
Mocha's struggles aside, decompilers generally render source fairly accurately. Once you know a decompiler's weaknesses, you can manually analyze and tweak the decompiled code to come up with a fairly accurate representation of the original. Add to that the fact that decompilers are getting better all the time, and we have a bit of a problem: What if you don't want anyone to be able to decompile your code?
Not only have decompilation and obfuscation techniques become more intricate over the past five years, but the interfaces to them are becoming increasingly slick. Several of the more recent decompilers let you browse through a directory of .class files and decompile them with a single click.
JODE (Java Optimize and Decompile Environment) is one such program. Type the name of a .jar file into the command line and JODE will allow you to graphically browse its classes, automatically decompiling each class for you to see. This is particularly useful for looking through the source code to libraries supplied with your Java SDK. Simply type in the following command:
$ java jode.swingui.Main --classpath [path to your Java SDK]/jre/lib/rt.jar
And you'll get a nice, smooth rendering of the file, as shown in Figure 1.

Sunday, August 31, 2008
Saturday, August 16, 2008
Cool Firefox Tricks That Might Make You Crazy
Some Cool Firefox Tricks That Might Make You Crazy!!
* chrome://browser/content/browser.xul :: Opens another Firefox inside a tab in the the existing Firefox window.
* chrome://browser/content/preferences/preferences.xul :: Opens the Options dialog box inside the Firefox tab.
* chrome://browser/content/bookmarks/bookmarksPanel.xul :: Opens the “Book Marks Manager” inside a tab in the Firefox window.
* chrome://browser/content/history/history-panel.xul :: Opens the History Panel in the Firefox tab.
* chrome://mozapps/content/extensions/extensions.xul?type=extensions :: Opens the Extensions window in the current tab.
* chrome://browser/content/preferences/cookies.xul :: Opens the “cookies window” inside a tab in the Firefox window.
* chrome://browser/content/preferences/sanitize.xul :: Opens the “Clear Private Data” window inside the current tab.
* chrome://browser/content/aboutDialog.xul :: Opens the “About Firefox” Dialog box inside the tab.
* chrome://browser/content/credits.xhtml :: A scrolling list of names. The one’s who we must thank for creating Firefox
And My favorite
* chrome://global/content/alerts/alert.xul :: Dancing Firefox.
* chrome://browser/content/browser.xul :: Opens another Firefox inside a tab in the the existing Firefox window.
* chrome://browser/content/preferences/preferences.xul :: Opens the Options dialog box inside the Firefox tab.
* chrome://browser/content/bookmarks/bookmarksPanel.xul :: Opens the “Book Marks Manager” inside a tab in the Firefox window.
* chrome://browser/content/history/history-panel.xul :: Opens the History Panel in the Firefox tab.
* chrome://mozapps/content/extensions/extensions.xul?type=extensions :: Opens the Extensions window in the current tab.
* chrome://browser/content/preferences/cookies.xul :: Opens the “cookies window” inside a tab in the Firefox window.
* chrome://browser/content/preferences/sanitize.xul :: Opens the “Clear Private Data” window inside the current tab.
* chrome://browser/content/aboutDialog.xul :: Opens the “About Firefox” Dialog box inside the tab.
* chrome://browser/content/credits.xhtml :: A scrolling list of names. The one’s who we must thank for creating Firefox
And My favorite
* chrome://global/content/alerts/alert.xul :: Dancing Firefox.
Tuesday, August 12, 2008
Get your orkut scraps delivered to your mobile
This article provides you with a very simple method to get orkut scraps delivered directly into your mobile phone as sms messages. The pages you may subscribe are scrapbook, community pages or even community messages. All the messages will be delivered free of cost. Following are the steps to get any orkut page as sms to mobile :
Register your mobile phone to MyToday. MyToday supports almost all networks in India.
Login to your orkut account and navigate to the page to which you wish to subscribe.
Copy the URL of the above page. It should be copied completely including http://. URL can be found in the address bar (where you enter www.orkut.com) of your browser.
In other window/ tab, open the orkutfeeds site and in the field provided, paste the above orkut URL and click on subscribe.
Now, copy the URL of subscription page as said above.
Open your MyToday account, and navigate to a page as seen in the snap in the following way.
a. Under My tab, click on feeds.
b. Under My Folders, click on Manage feeds.
c. Under Folders tab, click on SMS.
d. You will now get into a page.
Enter the name as you wish. Say, “My scraps” and at the URL field, paste the URL which you have copied from orkutfeeds subscription page, check Send SMS, click Create.
You’re done! Now, you can expect your scraps delivered into your mobile phone as and when your scrapbook updates.
You may use following methods to get your scrap directed to your mobile phone.
1. Determine your cell phone’s email id and use RSSFWD to send scrapbook feed updates to your mobile phone. Easiest way to determine your mobile phone’s email id is to send an email from your cell phone to your mail id (it costs you ) and look for from address in mail. In RSSFWD, you need to enter your cell phone’s mail id instead of your email id.
2. Yahoo! Alerts:
This is quite simple, you need to register your mobile for Yahoo! Mobile or Yahoo! Messenger. Goto Yahoo! Alerts page for feeds. Enter the feed url for your orkut scrapbook and select your mobile device to receive alerts. This trick did not work for me when I used my messenger phone (Spice, Karnataka, India.) to receive alerts. My network is compatible with messenger but did not work for alerts. For detailed description of using Yahoo! Alerts, I recommend you reading this post.
3. We have few more sites like SendMeRss or MyToday(India) or any other applicable for your geographic location. Just use the same trick, use the feed generated by orkut feeds and subscribe to that using any services like the ones above mentioned. Or use your cell phone’s email address and signup for that mail notification.
Register your mobile phone to MyToday. MyToday supports almost all networks in India.
Login to your orkut account and navigate to the page to which you wish to subscribe.
Copy the URL of the above page. It should be copied completely including http://. URL can be found in the address bar (where you enter www.orkut.com) of your browser.
In other window/ tab, open the orkutfeeds site and in the field provided, paste the above orkut URL and click on subscribe.
Now, copy the URL of subscription page as said above.
Open your MyToday account, and navigate to a page as seen in the snap in the following way.
a. Under My tab, click on feeds.
b. Under My Folders, click on Manage feeds.
c. Under Folders tab, click on SMS.
d. You will now get into a page.
Enter the name as you wish. Say, “My scraps” and at the URL field, paste the URL which you have copied from orkutfeeds subscription page, check Send SMS, click Create.
You’re done! Now, you can expect your scraps delivered into your mobile phone as and when your scrapbook updates.
You may use following methods to get your scrap directed to your mobile phone.
1. Determine your cell phone’s email id and use RSSFWD to send scrapbook feed updates to your mobile phone. Easiest way to determine your mobile phone’s email id is to send an email from your cell phone to your mail id (it costs you ) and look for from address in mail. In RSSFWD, you need to enter your cell phone’s mail id instead of your email id.
2. Yahoo! Alerts:
This is quite simple, you need to register your mobile for Yahoo! Mobile or Yahoo! Messenger. Goto Yahoo! Alerts page for feeds. Enter the feed url for your orkut scrapbook and select your mobile device to receive alerts. This trick did not work for me when I used my messenger phone (Spice, Karnataka, India.) to receive alerts. My network is compatible with messenger but did not work for alerts. For detailed description of using Yahoo! Alerts, I recommend you reading this post.
3. We have few more sites like SendMeRss or MyToday(India) or any other applicable for your geographic location. Just use the same trick, use the feed generated by orkut feeds and subscribe to that using any services like the ones above mentioned. Or use your cell phone’s email address and signup for that mail notification.
Tuesday, August 5, 2008
Finding and Ripping Template Monsters
Tools Needed:
-Browser with Google opened
-Black Widow Program v5.21 or Higher
http://rapidshare.com/files/63746479/BlackWidow5.21.rar
-Winrar
The process:
1. Open your browser up to Google.com
2. Paste one of the following lines into the search bar. Then hit enter.
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(*-b.jpg) +screenshots
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(psd) +sources
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(psd) +source
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(psd) +With_fl
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(psd) +site_flash
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(psd) +b.jpg
3. Now you will see a bunch of index's returned. This means the people were dumb and uploaded their whole Template, PSD's and all and didn't even have an index.html or index.php. Not everything returned is going to be a Template Monster Template. About 2/3 of them will be either garbage and not work, or some other random templates they made for their site. However you can easily tell the difference by the Google Description. If there is a 4-5 digit number like my example picture below (5622), then its probably a Template Monster.
4. Hit Parent Directory until you see folders like: "Sources, PSD, Screenshots, ClipArt, Flash, or Fonts. This is usually the main directory for that Template Monster. Copy and paste the URL from your browser into the BlackWidow Program. Once you paste it in there, hit enter and the site will load in the BlackWidow using IE. Now Click on the Structure Tab and Hit Scan at the top. Scanning should take 2-3min. If it takes any longer, its probably done and you can just hit stop and stop it manually.
5. Once its done scanning, Go back to the structure tab, and it has the whole site laid out. Now just highlight the folder right under the http:// folder on the left side and hit the download button.

6. A download menu will now come open. Download it to a any folder. However make sure your check boxes on the right are the same as mine below.

7. For some reason BlackWidow Downloads some useless junk files. You can easily delete them. All the files pictured below are garbage and can be done away with. Its probably best to keep all other files unless you know what your doing.

8. Now just rename the folder it made from the url to the TM # and zip or rar it up using Winrar.
-Browser with Google opened
-Black Widow Program v5.21 or Higher
http://rapidshare.com/files/63746479/BlackWidow5.21.rar
-Winrar
The process:
1. Open your browser up to Google.com
2. Paste one of the following lines into the search bar. Then hit enter.
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(*-b.jpg) +screenshots
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(psd) +sources
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(psd) +source
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(psd) +With_fl
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(psd) +site_flash
-inurl:htm -inurl:html -inurl:asp intitle:"index of" +(psd) +b.jpg
3. Now you will see a bunch of index's returned. This means the people were dumb and uploaded their whole Template, PSD's and all and didn't even have an index.html or index.php. Not everything returned is going to be a Template Monster Template. About 2/3 of them will be either garbage and not work, or some other random templates they made for their site. However you can easily tell the difference by the Google Description. If there is a 4-5 digit number like my example picture below (5622), then its probably a Template Monster.
4. Hit Parent Directory until you see folders like: "Sources, PSD, Screenshots, ClipArt, Flash, or Fonts. This is usually the main directory for that Template Monster. Copy and paste the URL from your browser into the BlackWidow Program. Once you paste it in there, hit enter and the site will load in the BlackWidow using IE. Now Click on the Structure Tab and Hit Scan at the top. Scanning should take 2-3min. If it takes any longer, its probably done and you can just hit stop and stop it manually.
5. Once its done scanning, Go back to the structure tab, and it has the whole site laid out. Now just highlight the folder right under the http:// folder on the left side and hit the download button.

6. A download menu will now come open. Download it to a any folder. However make sure your check boxes on the right are the same as mine below.

7. For some reason BlackWidow Downloads some useless junk files. You can easily delete them. All the files pictured below are garbage and can be done away with. Its probably best to keep all other files unless you know what your doing.

8. Now just rename the folder it made from the url to the TM # and zip or rar it up using Winrar.
Sunday, August 3, 2008
How To Make Your Own Radio Station
Must HAVE Winamp (Any Version)
First, things First your speed has to be at least 256/64 kbps (which means Dial-up users, will have alot of latency, just dnt bother)
Second, your going to have to have a domain, an updated one with the current i.p active. (Could be anything e.g. My sig)
Now, Your gonna have to download the Shoutcast Files.
Go to www.shoutcast.com to get the files.
Ok After downloading these, installing Both of them in any order i dnt care. Go to START>PROGRAM FILES>SHOUTcast DNAS>EDIT SHOUTCAST DNS CONFIG.
Ok your gonna have to Configure it:
Go Down and where it says password: change (that means your gonna have to change it to whatever, make sure u remember)
The Portbase: change it to whatever port you want it
Maxusers: (lets be realistic here, dnt put in 10000, like NXS's radio station) your bandwidth has to be extremely good, if your cable, 50 user max is ok, ADSL should stay below 10 users, and T1 connections should do whatever tickles there fantasy.
Open winamp, RIGHT CLICK>OPTIONS>PREFRENCES>DSP EFFECT> and choose the NULLSOFT SHOUTCAST.
Go to OUTPUT, and then click on Connection, Through the ADDRESS, type your address which you have done through www.no-ip.com, PORT NUMBER, whatever u did in the EDIT.txt, and your password.
Then go to Encoder, and choose your quality of your music. Go back to OUTPU>OUTPUT CONFIG> YELLOW PAGES. this is your advertisemant information. dow hatever you like there.
Now Connect. to check that your Radio os on-line go to http://(your address that you added in the prefrence)
First, things First your speed has to be at least 256/64 kbps (which means Dial-up users, will have alot of latency, just dnt bother)
Second, your going to have to have a domain, an updated one with the current i.p active. (Could be anything e.g. My sig)
Now, Your gonna have to download the Shoutcast Files.
Go to www.shoutcast.com to get the files.
Ok After downloading these, installing Both of them in any order i dnt care. Go to START>PROGRAM FILES>SHOUTcast DNAS>EDIT SHOUTCAST DNS CONFIG.
Ok your gonna have to Configure it:
Go Down and where it says password: change (that means your gonna have to change it to whatever, make sure u remember)
The Portbase: change it to whatever port you want it
Maxusers: (lets be realistic here, dnt put in 10000, like NXS's radio station) your bandwidth has to be extremely good, if your cable, 50 user max is ok, ADSL should stay below 10 users, and T1 connections should do whatever tickles there fantasy.
Open winamp, RIGHT CLICK>OPTIONS>PREFRENCES>DSP EFFECT> and choose the NULLSOFT SHOUTCAST.
Go to OUTPUT, and then click on Connection, Through the ADDRESS, type your address which you have done through www.no-ip.com, PORT NUMBER, whatever u did in the EDIT.txt, and your password.
Then go to Encoder, and choose your quality of your music. Go back to OUTPU>OUTPUT CONFIG> YELLOW PAGES. this is your advertisemant information. dow hatever you like there.
Now Connect. to check that your Radio os on-line go to http://(your address that you added in the prefrence)
Saturday, August 2, 2008
Changing Fraud Money to Real Money
More and more people nowadays get hacked CCs (Credit Cards), Paypals etc. However, what many don’t know is that they can actually cash out the fraud money, instead of just buying real life items, shipping it to their house and selling it. A very fast method would be as suggested.
Join this game*/Download it/ Go to it http://secondlife.com
Put fake info + your CC
Under Linden (Game Currency), Buy Linden Dollars, Click Transfer Linden Money to paypal
*Note: This is an ADULT game, meaning if you are under 18, it is not suggested you download this.
That’s all there is! Simply wait a few days, get legit paypal cash. (Advised not to do over 100 USD a day, and not to cash out the money immediately after your recieved it)
Optional (Safety Tips):
Purposely lose, gain cash to yourself/friends, to make the entire process seem more believable.
If you are losing cash to yourself, use PROXIES
Try to get the money OUT of the paypal as soon as possible
Source:Unkn0wn.eu
Join this game*/Download it/ Go to it http://secondlife.com
Put fake info + your CC
Under Linden (Game Currency), Buy Linden Dollars, Click Transfer Linden Money to paypal
*Note: This is an ADULT game, meaning if you are under 18, it is not suggested you download this.
That’s all there is! Simply wait a few days, get legit paypal cash. (Advised not to do over 100 USD a day, and not to cash out the money immediately after your recieved it)
Optional (Safety Tips):
Purposely lose, gain cash to yourself/friends, to make the entire process seem more believable.
If you are losing cash to yourself, use PROXIES
Try to get the money OUT of the paypal as soon as possible
Source:Unkn0wn.eu
Thursday, July 31, 2008
Test Your Website in all major browsers and OS in 1 go
Sometimes user make a website and release it....suddenly he got a eMail visitors are unable to open your website but its working perfect your side...ohhh...problem is web browser....so here is a good solution to Test your site before make it release
http://browsershots.org/
http://browsershots.org/
Tuesday, July 29, 2008
Mystery thumbs.db
Are you working as a cyber crime investigator and looking for something which can prove in court of law that there was some pornographic content on the suspect’s machine? Let me help you out in this case.There is a file with a name “thumbs.db” which is automatically generated by Windows XP whenever user views the folder or image in thumbs view or in filmstrip view. Automatic generation of this file is ON by default. Thumbs.db contains a copy of each of the tiny preview images generated for image files in that folder so that they load up quickly the next time you browse that folder. If a user tries to view this file by any image viewer then it will be of no use. For extracting the juicy content from this file, forensic investigator has to understand the header of the thumbs file present in thumbs.db. Let me explain step by step on how to extract useful content from thumbs.db file.
Open any folder which has got some jpeg files and make that folder view in thumbs view as shown in

As soon as the folder is kept in thumbs view “thumbs.db” file is created. Even if all JPEG files are deleted and thumbs.db file corresponding to those JPEG files is present, then also you can see the images but they will be very small in size. Thumbs.db which was created is now viewed using winhex. Once the file has been opened in winhex view, we will search and select for particular header. Header is “ÿØÿà JFIF” and its hex values are “FFD8FFE000104A464946″. This is shown in an example :-

Copy the entire content in a notepad where the header is starting till the end of the file and save the file with the extension JPEG. You can now easily view the extracted content with any of the image viewer. If there are large number of headers in thumbs.db file, then you can use professional tool like “Windows File Analyzer” to see the contents of thumbs.db file.
Open any folder which has got some jpeg files and make that folder view in thumbs view as shown in

As soon as the folder is kept in thumbs view “thumbs.db” file is created. Even if all JPEG files are deleted and thumbs.db file corresponding to those JPEG files is present, then also you can see the images but they will be very small in size. Thumbs.db which was created is now viewed using winhex. Once the file has been opened in winhex view, we will search and select for particular header. Header is “ÿØÿà JFIF” and its hex values are “FFD8FFE000104A464946″. This is shown in an example :-

Copy the entire content in a notepad where the header is starting till the end of the file and save the file with the extension JPEG. You can now easily view the extracted content with any of the image viewer. If there are large number of headers in thumbs.db file, then you can use professional tool like “Windows File Analyzer” to see the contents of thumbs.db file.
Hack your Recycle Bin

Have you ever thought of what happens when you hit the delete button?
Delete: When we simply delete a file we are throwing that file in the recycle bin of that particular volume. For example, if file resides in C:\ drive having FAT32 as file system and we delete a file of C:\ drive then that file will move to C:\Recycled. But if it is an NTFS volume then the file will move to \Recycler\.
Shift+Delete: When we hit Shift+Delete the file will not move to Recycled or Recycler. Instead it will by pass these two folders and will simply be deleted. In such scenarios the user does not have an option to restore a file from these two folders.
However forensics tells us the files are NOT actually deleted. The deleted files still exist on the hard disk but the pointer pointing to that file is deleted. The pointer information is stored by the INFO2 record which cannot be seen by a normal user. To view the INFO2 file use ATTRIB -r -s -h info2. We can also use a third party tool like for rifiuti to see whats written in the INFO2 file. Italian dictionary says rifiuti means trash. Thanks to Keith J. Jones for developing this wonderful tool. Rifuti can be downloaded from :- http://www.foundstone.com/us/resources/termsofuse.asp?file=rifiuti.zip
Check the Image below

In Encase one can use Enscripts to find information from INFO2 records. For local machine he can run “Scan local machine” enscript (Encase5) with Recycle Bin Info Record finder module selected. If a user is working on some image then he can simply run “Sweep Case” enscript with Recycle Bin Info Record finder module selected. All the information collected by Encase will be located in the bookmark tab.
All forensic investigators should definitely look for INFO2 record to gather crucial information. There is a good chance of the INFO2 record solving the case, ridding the investigator of further toil.

Sunday, June 22, 2008
Increase your Google Ranks
Author:Guido Nussbaum
Today I have something very special for you... I'll show you how you can get top 10 positions in google within a couple of days.
It's the exact same technique that I've used to rank one of my websites for the search term "jv giveaway script". Go to google and search for it... you'll see that I have position 1, 2, 4, 8 and many more... all ranked within less than a week!
Actually I had planned to write a complete ebook or report about this but I'm currently to busy with all my projects. So I've decided to give this strategy to my valued subscribers instead of selling it. It's my way to say Thank You for reading my emails.
Are you ready? Well then let's go...
Step 1: Find Keywords with less than 100.000 competing websites
Tools: Wordtracker
Step 2: Register a domain that includes your keyword.
Example: I found the keyword "Pakistani Cooking" and want to rank for this term. So I go and register the domains www.pakistani-cooking.com or www.pakistanicooking.com
Step 3: Build your website and include your keyword on your index page in the title and in the first sentence of your body text.
Suggestion: Use Wordpress to build your website. A website on wordpress is preferred by google and naturally ranks higher.
Step4: Bookmark your website. Use as many bookmarking services as possible to get many 1-way links.
Suggestion: You can use www.socialposter.com or www.socialmarker.com to speed up your bookmarking process.
Step 5: Write one or more articles including your keyword again in the title and the first sentence. Submit your articles to as many article directories as possible.
Suggestion: You can use ISnare to automatically distribute your articles to hundreds of directories. http://www.plr-niches.com/presents/isnare.htm
Step 6: Create one or more Squidoo lenses. Again, include your keyword in the title and the first sentence. If possible include the keyword in your lense domain. You can also use your keyword and variations of it in the Tags of your lense.
Start to build your lense here: http://www.plr-niches.com/presents/squidoo.htm
Step 7: Bookmark your Squidoo lense just like you bookmarked your website in step 4
Step 8: Submit your website to as many directories as possible.
Suggestion: Use the semi-automated DigiXmas Submitter at http://www.plr-niches.com/presents/digixmas.htm
That's it! If you have chosen the right keyword, then your website, your squidoo lense and your bookmarks will appear all over the first pages in google and other search engines. If you have chosen a keyword with higher competition, then you simply need to build up more backlinks by creating more squidoo lenses and by submitting more articles.
If you are new to internet marketing, then you might not completely understand why to do certain things in the strategy above. All I can say here is Just Do It... it works.
Today I have something very special for you... I'll show you how you can get top 10 positions in google within a couple of days.
It's the exact same technique that I've used to rank one of my websites for the search term "jv giveaway script". Go to google and search for it... you'll see that I have position 1, 2, 4, 8 and many more... all ranked within less than a week!
Actually I had planned to write a complete ebook or report about this but I'm currently to busy with all my projects. So I've decided to give this strategy to my valued subscribers instead of selling it. It's my way to say Thank You for reading my emails.
Are you ready? Well then let's go...
Step 1: Find Keywords with less than 100.000 competing websites
Tools: Wordtracker
Step 2: Register a domain that includes your keyword.
Example: I found the keyword "Pakistani Cooking" and want to rank for this term. So I go and register the domains www.pakistani-cooking.com or www.pakistanicooking.com
Step 3: Build your website and include your keyword on your index page in the title and in the first sentence of your body text.
Suggestion: Use Wordpress to build your website. A website on wordpress is preferred by google and naturally ranks higher.
Step4: Bookmark your website. Use as many bookmarking services as possible to get many 1-way links.
Suggestion: You can use www.socialposter.com or www.socialmarker.com to speed up your bookmarking process.
Step 5: Write one or more articles including your keyword again in the title and the first sentence. Submit your articles to as many article directories as possible.
Suggestion: You can use ISnare to automatically distribute your articles to hundreds of directories. http://www.plr-niches.com/presents/isnare.htm
Step 6: Create one or more Squidoo lenses. Again, include your keyword in the title and the first sentence. If possible include the keyword in your lense domain. You can also use your keyword and variations of it in the Tags of your lense.
Start to build your lense here: http://www.plr-niches.com/presents/squidoo.htm
Step 7: Bookmark your Squidoo lense just like you bookmarked your website in step 4
Step 8: Submit your website to as many directories as possible.
Suggestion: Use the semi-automated DigiXmas Submitter at http://www.plr-niches.com/presents/digixmas.htm
That's it! If you have chosen the right keyword, then your website, your squidoo lense and your bookmarks will appear all over the first pages in google and other search engines. If you have chosen a keyword with higher competition, then you simply need to build up more backlinks by creating more squidoo lenses and by submitting more articles.
If you are new to internet marketing, then you might not completely understand why to do certain things in the strategy above. All I can say here is Just Do It... it works.
Sunday, May 18, 2008
Sites for tranfering money from credit cards
www.xoom.com
www.workgateways.com
www.moneybookers.com
www.foreignborn.com
www.ifad.org
www.overseasmoneytransfersite.com
www.workgateways.com
www.moneybookers.com
www.foreignborn.com
www.ifad.org
www.overseasmoneytransfersite.com
Wednesday, April 23, 2008
Save Time When Copying Mutiple Files
Download Piki basketfirst:--
CODE
http://www.conceptworld.com/Piky/PkySetup.exe
When copying files if they are located at different folders (places), going to each folder, copying files and then pasting in the destination is one hefty task. Piky Basket is one handy utility which extends the default copy paste functionalities of Windows.

Using Piky Basket, you can put the files in a virtual basket, and then paste them in the destination. It makes organizing the files easier, you can just right click on the files, add them to the virtual basket, and then paste them in one go. This is a great time saver when you're selecting files for backup, or sharing or to burn them on CD etc.
It reduces the repetitive tasks when copying or moving files and folders in Windows. You can also copy folders/files path on the clipboard and paste them in text file. You can even launch the command prompt from any folder. Since it gets integrated within Windows and works from the shell, it doesn't use any resources.
In fact, you don't even need to run it as a separate program. It is a must for everyone.
there are some mosre uses of Piky basket
like
coppying file paths etc etc..
CODE
http://www.conceptworld.com/Piky/PkySetup.exe
When copying files if they are located at different folders (places), going to each folder, copying files and then pasting in the destination is one hefty task. Piky Basket is one handy utility which extends the default copy paste functionalities of Windows.

Using Piky Basket, you can put the files in a virtual basket, and then paste them in the destination. It makes organizing the files easier, you can just right click on the files, add them to the virtual basket, and then paste them in one go. This is a great time saver when you're selecting files for backup, or sharing or to burn them on CD etc.
It reduces the repetitive tasks when copying or moving files and folders in Windows. You can also copy folders/files path on the clipboard and paste them in text file. You can even launch the command prompt from any folder. Since it gets integrated within Windows and works from the shell, it doesn't use any resources.
In fact, you don't even need to run it as a separate program. It is a must for everyone.
there are some mosre uses of Piky basket
like
coppying file paths etc etc..
WinUtuxU OS with SP2 (Windows & Linux in One CD)


Included :
JRE-5.0-Update-6
gtk+-2.10.13
Python-2.5.1
vcredist
dotnetfx-2.0
InfraRecorder-0.43.1
cdrtfe-1.3
CdFly-0.3
7zip-4.51
peazip-1.8.2
Gimp-2.2.17
Blender-2.44
Inkscape-0.45.1
ImageMagick-6.3.4
frozen_bubble-1.0.0
supertux-0.3.0
tuxracer
sudoku-easy
clamwin-0.91.1
FireFox-2.0.0.5
Thunderbird-2.0.0.5
Sunbird-0.5
httrack-3.41
nvu-1.0
Pidgin-2.0.2
TrueDownloader-0.82
Audacity-1.3.3
Traverso-0.40.0
AviDemux-2.4
Vivia-0.1
OpenOffice-2.2.1
NotePad++-4.1.2: SumatraPDF-0.6
vlc-0.8.6c
KMPlayer-2.9.3.1304
SMPlayer-0.5.21
Songbird-0.2
winmd5sum
Download:
http://rapidshare.com/files/67355003/WinUtuxU_OS.part1.rar
http://rapidshare.com/files/67358260/WinUtuxU_OS.part2.rar
http://rapidshare.com/files/67359815/WinUtuxU_OS.part3.rar
http://rapidshare.com/files/67361093/WinUtuxU_OS.part4.rar
http://rapidshare.com/files/67362243/WinUtuxU_OS.part5.rar
http://rapidshare.com/files/67363777/WinUtuxU_OS.part6.rar
http://rapidshare.com/files/67365229/WinUtuxU_OS.part7.rar
Friday, February 8, 2008
how to create an .exe file
many of u might be knowing this but still this is for those who dont know
Making an executable file(.exe)
goto to start run and type iexpress
STEP BY STEP ON HOW TO USE IT
click create new self extraction then next
click extract files and run an installation command and click next
type what you want to name the files then click next
click no prompt then next
license agreement unless you want to put one click do not display license
package files(most important) click add then choose your .bat file(also does .vbs files) then click next
under install program choose your .bat or .vbs file and click next
show window pick one and click next
finished message pick one and click next
click browse and type the name of it and save then next
configure restart just click no restart and then next
just click don't save then next
their click next and watchyour file change into something better
when its done click finish and check out your new file
Making an executable file(.exe)
goto to start run and type iexpress
STEP BY STEP ON HOW TO USE IT
click create new self extraction then next
click extract files and run an installation command and click next
type what you want to name the files then click next
click no prompt then next
license agreement unless you want to put one click do not display license
package files(most important) click add then choose your .bat file(also does .vbs files) then click next
under install program choose your .bat or .vbs file and click next
show window pick one and click next
finished message pick one and click next
click browse and type the name of it and save then next
configure restart just click no restart and then next
just click don't save then next
their click next and watchyour file change into something better
when its done click finish and check out your new file
Block websites without any software
block webSites without any Softwares !!__________________________________________________________
Steps
1] Browse C:\WINDOWS\system32\drivers\etc
2] Find the file named "HOSTS"
3] Open it in notepad
4] Under "127.0.0.1 localhost" Add 127.0.0.2 www.orkut.com , and that site will no longer be accessable.
5] Done!
example :
127.0.0.1 localhost
127.0.0.2 www.orkut.com
- www.orkut.com is now unaccessable
For every site after that you want to add, just add "1" to the last number in the internal ip (127.0.0.2) and then the addy like before.
IE:
127.0.0.3 www.yahoo.com
127.0.0.4 www.msn.com
127.0.0.5 www.google.com
This also works with banner sites, just find the host name of the server with the banners and do the same thing with that addy.
Hoep this small tutorial could keep you going in simple way of blocking websites
Steps
1] Browse C:\WINDOWS\system32\drivers\etc
2] Find the file named "HOSTS"
3] Open it in notepad
4] Under "127.0.0.1 localhost" Add 127.0.0.2 www.orkut.com , and that site will no longer be accessable.
5] Done!
example :
127.0.0.1 localhost
127.0.0.2 www.orkut.com
- www.orkut.com is now unaccessable
For every site after that you want to add, just add "1" to the last number in the internal ip (127.0.0.2) and then the addy like before.
IE:
127.0.0.3 www.yahoo.com
127.0.0.4 www.msn.com
127.0.0.5 www.google.com
This also works with banner sites, just find the host name of the server with the banners and do the same thing with that addy.
Hoep this small tutorial could keep you going in simple way of blocking websites
Career Academy Hacking, Penetration Testing and Counter 17CD
Package Includes:
Featuring live instructor-led classroom sessions with full audio, video and demonstration components
Printable courseware
300+ Penetration Testing Review Questions
eWorkbook - 725 pages Student eWorkbook by Logical Security
Module 1
Ethical Hacking and Penetration Testing
Security 101
Hacking Hall of Fame
What are Today's hackers Like?
Today's Hackers
Risk Management
Evolution of Threats
Typical Vulnerability Life Cycle
What is Ethical Hacking?
Rise of the Ethical Hacker
Types of Security Test
Penetration Test (Pen-test)
Red Teams
Testing Methodology
VMWare Workstation
Wind0wz and Linux Running VMWare
Linux Is a Must
Linux Survival Skills
Useful vi Editor Commands
Module 1 Review
Module 2
Footprinting and Reconnaissance
Desired Information
Find Information by the Target (Edgar)
terraserver.M'***zoft.com
Network Reconnaissance & DNS Search
Query Whois Databases
Command-Line Whois Searches
ARIN whois: Search IP Address Blocks
SamSpade Tool and Website
Internet Presence
Look Through Source Code
Mirror Website
Find Specific Types of Systems
Big Brother
AltaV_I_S_T_A
Specific Data Being Available?
Anonymizers
Countermeasures to Information Leakage
Social Engineering
DNS Zone Transfer
Nslookup command-line utility
Zone Transfer from Linux
Automated Zone Transfers
Zone Transfer Countermeasures
www.CheckDNS.net
Tracing Out a Network Path
tracert Output
Free Tools
Paratrace
War Dialing for Hanging Modems
Manual and Automated War Dialing
Case Study
www.guidedogs.com
Footprinting Countermeasures
Demo - Footprinting & Info Gathering
Module 2 Review
Module 3
TCP/IP Basics and Scanning
The OSI Model
TCP/IP Protocol Suite Layers
Encapsulation
Data-Link Protocols
IP - Internet Protocol, Datagram (Packet)
ICMP Packets
UDP – User Datagram Protocol
UDP Datagram
TCP – Transmission Control Protocol
TCP Segment
TCP/IP 3-Way Handshake and Flags
TCP and UDP Ports
Ping Sweeps
Good Old Ping, Nmap, TCP Ping Sweep
TCP Sweep Traffic Captured
Unix Pinging Utilities
Default TTLs
Pinging Countermeasures
Port Scanning
Nmap
Advanced Probing Techniques
Scanrand
Port Probing Countermeasures
Watch Your Own Ports
Demo - Scanning Tools
Module 3 Review
Module 4
Enumeration and Verification
Operating System Identification
Differences Between OS TCP/IP Stack
Nmap -O
Active vs Passive Fingerprinting
Xprobe/Xprobe2
Countermeasures
SNMP Overview
SNMP Enumeration
SMTP, Finger, and E-mail Aliases
Gleaning Information from SMTP
SMTP E-mail Alias Enumeration
SMTP Enumeration Countermeasures
CIFS/SMB
Attack Methodology
Find Domains and Computers
NetBIOS Data
NBTscan
NULL Session
Local and Domain Users
Find Shares with net view
enum: the All-in-one
Winfo and NTInfoScan (ntis.exe)
Digging in the Registry
NetBIOS Attack Summary
NetBIOS Countermeasures
What’s this SID Thing Anyway?
Common SIDs and RIDs
whoami
RestrictAnonymous
USER2SID/SID2USER
psgetsid.exe and UserDump Tool
LDAP and Active Directory
GUI Tools to Perform the Same Actions
Demo - Enumeration
Module 4 Review
Module 5
Hacking & Defending Wireless/Modems
Phone Numbers & Modem Background
Phone Reconnaissance
Modem Attacks
Wireless Reconnaissance
Wireless Background
Wireless Reconnaissance Continued
Wireless Sniffing
Cracking WEP Keys
Defending Wireless
Module 5 Review
Module 6
Hacking & Defending Web Servers
Web Servers in General: HTTP
Uniform Resource Locator: URL
Apache Web Server Functionality
Apache: Attacking Mis-configurations
Apache: Attacking Known Vulnerabilities
Defending Apache Web Server
M'***zoft Internet Information Server (IIS)
IIS: Security Features
IIS: Attacking General Problems
IIS: IUSER or IWAM Level Access
IIS: Administrator or Sys Level Access
IIS: Clearing IIS Logs
IIS: Defending and Countermeasures
Web Server Vulnerability Scanners
Demo - Hacking Web Servers
Module 6 Review
Module 7
Hacking & Defending Web Applications
Background on Web Threat & Design
Basic Infrastructure Information
Information Leaks on Web Pages
Hacking over SSL
Use the Source, Luke…
Functional/Logic Testing
Attacking Authentication
Attacking Authorization
Debug Proxies: @stake webproxy
Input Validation Attacks
Attacking Session State
Attacking Web Clients
Cross-Site Scripting (XSS) Threats
Defending Web Applications
Module 7 Review
Module 8
Sniffers and Session Hijacking
Sniffers
Why Are Sniffers so Dangerous?
Collision & Broadcast Domains
VLANs and Layer-3 Segmentation
tcpdump & WinDump
Berkley Packet Filter (BPF)
Libpcap & WinPcap
BUTTSniffing Tool and dSniff
Ethereal
Mitigation of Sniffer Attacks
Antisniff
ARP Poisoning
MAC Flooding
DNS and IP Spoofing
Session Hijacking
Sequence Numbers
Hunt
Ettercap
Source Routing
Hijack Countermeasures
Demo - Sniffers
Module 8 Review
Module 9
Hacking & Defending Wind0wz Systems
Physical Attacks
LANMan Hashes and Weaknesses
WinNT Hash and Weaknesses
Look for Guest, Temp, Joe Accounts
Direct Password Attacks
Before You Crack: Enum Tool
Finding More Account Information
Cracking Passwords
Grabbing the SAM
Crack the Obtained SAM
LSA Secrets and Trusts
Using the Newly Guessed Password
Bruteforcing Other Services
Operating System Attacks
Hiding Tracks: Clearing Logs
Hardening Wind0wz Systems
Strong 3-Factor Authentication
Creating Strong Passwords
Authentication
Wind0wz Account Lockouts
Auditing Passwords
File Permissions
Demo - Attacking Wind0wz Systems
Module 9 Review
Module 10
Hacking & Defending Unix Systems
Physical Attacks on Linux
Password Cracking
Brute Force Password Attacks
Stack Operation
Race Condition Errors
Format String Errors
File System Attacks
Hiding Tracks
Single User Countermeasure
Strong Authentication
Single Sign-On Technologies
Account Lockouts
Shadow Password Files
Buffer Overflow Countermeasures
LPRng Countermeasures
Tight File Permissions
Hiding Tracks Countermeasures
Removing Unnecessary Applications
DoS Countermeasures
Hardening Scripts
Using SSH & VPNs to Prevent Sniffing
Demo - Attacking Unix Systems
Module 10 Review
Module 11
Rootkits, Backdoors, Trojans & Tunnels
Types Of Rootkits
A Look at LRK
Examples of Trojaned Files
Wind0wz NT Rootkits
NT Rootkit
AFX Wind0wz Rootkit 2003
Rootkit Prevention Unix
Rootkit Prevention Wind0wz
netcat
netcat: Useful Unix Commands
netcat: What it Looks Like
VNC-Virtual Network Computing
Backdoor Defenses
Trojans
Back Orifice 2000
NetBus
SubSeven
Defenses to Trojans
Tunneling
Loki
Other Tunnels
Q-2.4 by Mixter
Starting Up Malicious Code
Defenses Against Tunnels
Manually Deleting Logs
Tools to Modify Logs
Demo - Trojans
Module 11 Review
Module 12
Denial of Service and Botnets
Denial-of-Service Attacks
CPUHog
Ping of Death
Teardrop Attacks
Jolt2
Smurf Attacks
SYN Attacks
UDP Floods
Distributed DoS
DDoS Tool: Trin00
Other DDoS Variation
History of Botnets
Anatomy of a Botnet
Some Common Bots
Demo - Denial of Service
Module 12 Review
Module 13
Automated Pen Testing Tools
General: Definitions
General:What?
General: Why?
Core Impact™ Framework
Core Impact™ Operation
Canvas™ Framework
Canvas™ Operation
Metasploit Framework
Metasploit Operation
Demo - Automated Pen Testing
Module 13 Review
Module 14
Intrusion Detection Systems
Types of IDSs
Network IDSs
Distributed IDSs (DIDSs)
Anomaly Detection
Signature Detection
Common IDS Software Products
Introduction to Snort
Attacking an IDS
Eluding Techniques
Testing an IDS
Hacking Tool - NIDSbench
Hacking Tool - Fragroute
Hacking Tool - SideStep
Hacking Tool - ADMmutate
Other IDS Evasion Tools
Demo - IDS and Snort
Module 14 Review
Module 15
Firewalls
Firewall Types
Application Layer Gateways
ALGs (Proxies)
Stateful Inspection Engine
Hybrid Firewall
Host-Based Firewall
Network-Based Firewall
DMZ (Demilitarized Zone)
Back-to-Back Firewalls
Bastion Hosts
Control Traffic Flow
Multiple DMZs
Controlling Traffic Flow
Why Do I Need a Firewall?
What Should I Filter?
Egress Filtering
Network Address Translation (NAT)
Firewall Vulnerabilities
IPTables/NetFilter
Default Tables and Chains
iptables Syntax 1
iptables Syntax 2
Sample IPTables Script 1
Sample IPTables Script 2
Persistent Firewalls
Firewall Identification
Firewalk
Tunneling with Loki
Tunneling with NetCat/CryptCat
Port Redirection with Fpipe
Denial-of-Service Attacks Risk?
Demo - Firewalls and IP Tables
Module 15 Review
Module 16
Honeypots and Honeynets
What Is a Honeypot?
Advantages and Disadvantages
Types and Categories of Honeypots
Honeypot: Tarpits
Honeypot: Kfsensor
Honeypot: Honeyd
Sample Honeyd Configuration
High-Interaction Honeypot
Project HoneyNet
Types of Honeynets
The Main Difference is Data Control
GEN II Data Control: Honeywall CD
Gen II Data Capture: Sebek & Sebek II
Automated Alerting
Testing
Legal Issues
Demo - Setting up a Honeypot
Module 16 Review
Module 17
Ethics and Legal Issues
The Costs
Relation to Ethical Hacking?
The Dual Nature of Tools
Good Instead of Evil?
Recognizing Trouble When It Happens
Emulating the Attack
Security Does Not Like Complexity
Proper and Ethical Disclosure
CERT’s Current Process
Full Disclosure Policy
Organization for Internet Safety (OIS)
What Should We Do from Here?
Legal Meets Information Systems
Addressing Individual Laws
18 USC SECTION 1029
18 USC SECTION 1030
1030: Worms and Viruses
Blaster Worm Attacks
Civil vs. Criminal
18 USC SECTIONS 2510 and 2701
Digital Millennium Copyright Act
Cyber Security Enhancement Act
Module 17 Review
Course Closure
CD1.Ethical.Hacking.and.Penetration
Code:
http://rapidshare.com/files/24150271/Module_1.part01.rar
http://rapidshare.com/files/24150273/Module_1.part02.rar
http://rapidshare.com/files/24150275/Module_1.part03.rar
http://rapidshare.com/files/24150276/Module_1.part04.rar
http://rapidshare.com/files/24159635/Module_1.part05.rar
http://rapidshare.com/files/24159637/Module_1.part06.rar
http://rapidshare.com/files/24159638/Module_1.part07.rar
http://rapidshare.com/files/24159639/Module_1.part08.rar
http://rapidshare.com/files/24163957/Module_1.part09.rar
http://rapidshare.com/files/24163959/Module_1.part10.rar
CD2 Footprinting and Reconnaissance
Code:
http://rapidshare.com/files/24168655/Module_2.part01.rar
http://rapidshare.com/files/24168656/Module_2.part02.rar
http://rapidshare.com/files/24168657/Module_2.part03.rar
http://rapidshare.com/files/24168658/Module_2.part04.rar
http://rapidshare.com/files/24174114/Module_2.part05.rar
http://rapidshare.com/files/24174115/Module_2.part06.rar
http://rapidshare.com/files/24310589/Module_2.part07.rar
http://rapidshare.com/files/24310590/Module_2.part08.rar
http://rapidshare.com/files/24310591/Module_2.part09.rar
CD3 TCP/IP Basics and Scanning
Code:
http://rapidshare.com/files/24321107/mod.3.part1.rar
http://rapidshare.com/files/24321109/mod.3.part2.rar
http://rapidshare.com/files/24339724/mod.3.part3.rar
CD4 Enumeration and Verification
Code:
http://rapidshare.com/files/25291513/module.4.part1.rar
http://rapidshare.com/files/25291516/module.4.part2.rar
http://rapidshare.com/files/25297786/module.4.part3.rar
http://rapidshare.com/files/25297787/module.4.part4.rar
CD5 Hacking & Defending Wireless/Modems
Code:
http://rapidshare.com/files/24480780/module_5.part1.rar
http://rapidshare.com/files/24480781/module_5.part2.rar
http://rapidshare.com/files/24480784/module_5.part3.rar
http://rapidshare.com/files/24480785/module_5.part4.rar
http://rapidshare.com/files/24480786/module_5.part5.rar
http://rapidshare.com/files/24480787/module_5.part6.rar
CD6 Hacking & Defending Web Servers
Code:
http://rapidshare.com/files/28925031/Module.6.Hacking.Defending.Web.Servs.part01.rar
http://rapidshare.com/files/28925032/Module.6.Hacking.Defending.Web.Servs.part02.rar
http://rapidshare.com/files/28925034/Module.6.Hacking.Defending.Web.Servs.part03.rar
http://rapidshare.com/files/28925035/Module.6.Hacking.Defending.Web.Servs.part04.rar
http://rapidshare.com/files/28931012/Module.6.Hacking.Defending.Web.Servs.part05.rar
http://rapidshare.com/files/28931013/Module.6.Hacking.Defending.Web.Servs.part06.rar
CD7.Hacking.Defending.Web.Applications
Code:
http://rapidshare.com/files/26188740/Module.7.part1.rar
http://rapidshare.com/files/26188742/Module.7.part2.rar
http://rapidshare.com/files/26196529/Module.7.part3.rar
CD8. .Sniffers.and.Session.Hijacking
Code:
http://rapidshare.com/files/26196533/Module.8.part1.rar
http://rapidshare.com/files/26360406/Module.8.part2.rar
http://rapidshare.com/files/26360407/Module.8.part3.rar
CD9.Hacking.Defending.Wind0wz.Systems
Code:
http://rapidshare.com/files/26370153/Module.9.part1.rar
http://rapidshare.com/files/26376136/Module.9.part2.rar
http://rapidshare.com/files/26370156/Module.9.part3.rar
CD10.Hacking.Defending.Unix.Systems
Code:
http://rapidshare.com/files/28216732/Module_10.part01.rar
http://rapidshare.com/files/28216733/Module_10.part02.rar
http://rapidshare.com/files/28216734/Module_10.part03.rar
http://rapidshare.com/files/28216735/Module_10.part04.rar
http://rapidshare.com/files/28216737/Module_10.part05.rar
http://rapidshare.com/files/28216740/Module_10.part06.rar
http://rapidshare.com/files/28222043/Module_10.part07.rar
http://rapidshare.com/files/28222044/Module_10.part08.rar
http://rapidshare.com/files/28222045/Module_10.part09.rar
http://rapidshare.com/files/28222046/Module_10.part10.rar
CD .11.Rootkits.Backdoors.Trojans.Tunnels
Code:
http://rapidshare.com/files/28236225/Module_11.part01.rar
http://rapidshare.com/files/28236226/Module_11.part02.rar
http://rapidshare.com/files/28236228/Module_11.part03.rar
http://rapidshare.com/files/28236229/Module_11.part04.rar
http://rapidshare.com/files/28236231/Module_11.part05.rar
http://rapidshare.com/files/28236233/Module_11.part06.rar
http://rapidshare.com/files/28238956/Module_11.part07.rar
http://rapidshare.com/files/28238959/Module_11.part08.rar
CD.12.Denial.of.Service.and.Botnets
Code:
http://rapidshare.com/files/28250428/Module_12.part1.rar
http://rapidshare.com/files/28250430/Module_12.part2.rar
http://rapidshare.com/files/28250431/Module_12.part3.rar
http://rapidshare.com/files/28250432/Module_12.part4.rar
http://rapidshare.com/files/28250433/Module_12.part5.rar
http://rapidshare.com/files/28250434/Module_12.part6.rar
http://rapidshare.com/files/28250435/Module_12.part7.rar
CD.13..Automated.Pen.Testing.Tools
Code:
http://rapidshare.com/files/28259605/Module.13.part01.rar
http://rapidshare.com/files/28259607/Module.13.part02.rar
http://rapidshare.com/files/28259608/Module.13.part03.rar
http://rapidshare.com/files/28259610/Module.13.part04.rar
http://rapidshare.com/files/28259612/Module.13.part05.rar
http://rapidshare.com/files/28259613/Module.13.part06.rar
http://rapidshare.com/files/28259614/Module.13.part07.rar
CD.14.Intrusion.Detection.Systems
Code:
http://rapidshare.com/files/28268932/Module_14.part01.rar
http://rapidshare.com/files/28268933/Module_14.part02.rar
http://rapidshare.com/files/28268935/Module_14.part03.rar
http://rapidshare.com/files/28268936/Module_14.part04.rar
http://rapidshare.com/files/28268937/Module_14.part05.rar
http://rapidshare.com/files/28268938/Module_14.part06.rar
http://rapidshare.com/files/28275713/Module_14.part07.rar
http://rapidshare.com/files/28275714/Module_14.part08.rar
http://rapidshare.com/files/28275715/Module_14.part09.rar
http://rapidshare.com/files/28275716/Module_14.part10.rar
CD .15.Firewalls
Code:
http://rapidshare.com/files/28283458/Module_15.part01.rar
http://rapidshare.com/files/28283459/Module_15.part02.rar
http://rapidshare.com/files/28283460/Module_15.part03.rar
http://rapidshare.com/files/28283461/Module_15.part04.rar
http://rapidshare.com/files/28283464/Module_15.part05.rar
http://rapidshare.com/files/28283465/Module_15.part06.rar
http://rapidshare.com/files/28338024/Module_15.part07.rar
http://rapidshare.com/files/28338028/Module_15.part08.rar
http://rapidshare.com/files/28338029/Module_15.part09.rar
http://rapidshare.com/files/28338030/Module_15.part10.rar
http://rapidshare.com/files/28338032/Module_15.part11.rar
CD. 16.Honeypots.and.Honeynets
Code:
http://rapidshare.com/files/28345006/Module_16.part01.rar
http://rapidshare.com/files/28345007/Module_16.part02.rar
http://rapidshare.com/files/28345008/Module_16.part03.rar
http://rapidshare.com/files/28345009/Module_16.part04.rar
http://rapidshare.com/files/28345010/Module_16.part05.rar
http://rapidshare.com/files/28345011/Module_16.part06.rar
http://rapidshare.com/files/28354433/Module_16.part07.rar
http://rapidshare.com/files/28354435/Module_16.part08.rar
CD. 17 .Ethics.and.Legal.Issues
Code:
http://rapidshare.com/files/28354436/Module_17.part1.rar
http://rapidshare.com/files/28354437/Module_17.part2.rar
http://rapidshare.com/files/28354438/Module_17.part3.rar
http://rapidshare.com/files/28354439/Module_17.part4.rar
http://rapidshare.com/files/28357536/Module_17.part5.rar
http://rapidshare.com/files/28357537/Module_17.part6.rar
PASS included in rar file description
Featuring live instructor-led classroom sessions with full audio, video and demonstration components
Printable courseware
300+ Penetration Testing Review Questions
eWorkbook - 725 pages Student eWorkbook by Logical Security
Module 1
Ethical Hacking and Penetration Testing
Security 101
Hacking Hall of Fame
What are Today's hackers Like?
Today's Hackers
Risk Management
Evolution of Threats
Typical Vulnerability Life Cycle
What is Ethical Hacking?
Rise of the Ethical Hacker
Types of Security Test
Penetration Test (Pen-test)
Red Teams
Testing Methodology
VMWare Workstation
Wind0wz and Linux Running VMWare
Linux Is a Must
Linux Survival Skills
Useful vi Editor Commands
Module 1 Review
Module 2
Footprinting and Reconnaissance
Desired Information
Find Information by the Target (Edgar)
terraserver.M'***zoft.com
Network Reconnaissance & DNS Search
Query Whois Databases
Command-Line Whois Searches
ARIN whois: Search IP Address Blocks
SamSpade Tool and Website
Internet Presence
Look Through Source Code
Mirror Website
Find Specific Types of Systems
Big Brother
AltaV_I_S_T_A
Specific Data Being Available?
Anonymizers
Countermeasures to Information Leakage
Social Engineering
DNS Zone Transfer
Nslookup command-line utility
Zone Transfer from Linux
Automated Zone Transfers
Zone Transfer Countermeasures
www.CheckDNS.net
Tracing Out a Network Path
tracert Output
Free Tools
Paratrace
War Dialing for Hanging Modems
Manual and Automated War Dialing
Case Study
www.guidedogs.com
Footprinting Countermeasures
Demo - Footprinting & Info Gathering
Module 2 Review
Module 3
TCP/IP Basics and Scanning
The OSI Model
TCP/IP Protocol Suite Layers
Encapsulation
Data-Link Protocols
IP - Internet Protocol, Datagram (Packet)
ICMP Packets
UDP – User Datagram Protocol
UDP Datagram
TCP – Transmission Control Protocol
TCP Segment
TCP/IP 3-Way Handshake and Flags
TCP and UDP Ports
Ping Sweeps
Good Old Ping, Nmap, TCP Ping Sweep
TCP Sweep Traffic Captured
Unix Pinging Utilities
Default TTLs
Pinging Countermeasures
Port Scanning
Nmap
Advanced Probing Techniques
Scanrand
Port Probing Countermeasures
Watch Your Own Ports
Demo - Scanning Tools
Module 3 Review
Module 4
Enumeration and Verification
Operating System Identification
Differences Between OS TCP/IP Stack
Nmap -O
Active vs Passive Fingerprinting
Xprobe/Xprobe2
Countermeasures
SNMP Overview
SNMP Enumeration
SMTP, Finger, and E-mail Aliases
Gleaning Information from SMTP
SMTP E-mail Alias Enumeration
SMTP Enumeration Countermeasures
CIFS/SMB
Attack Methodology
Find Domains and Computers
NetBIOS Data
NBTscan
NULL Session
Local and Domain Users
Find Shares with net view
enum: the All-in-one
Winfo and NTInfoScan (ntis.exe)
Digging in the Registry
NetBIOS Attack Summary
NetBIOS Countermeasures
What’s this SID Thing Anyway?
Common SIDs and RIDs
whoami
RestrictAnonymous
USER2SID/SID2USER
psgetsid.exe and UserDump Tool
LDAP and Active Directory
GUI Tools to Perform the Same Actions
Demo - Enumeration
Module 4 Review
Module 5
Hacking & Defending Wireless/Modems
Phone Numbers & Modem Background
Phone Reconnaissance
Modem Attacks
Wireless Reconnaissance
Wireless Background
Wireless Reconnaissance Continued
Wireless Sniffing
Cracking WEP Keys
Defending Wireless
Module 5 Review
Module 6
Hacking & Defending Web Servers
Web Servers in General: HTTP
Uniform Resource Locator: URL
Apache Web Server Functionality
Apache: Attacking Mis-configurations
Apache: Attacking Known Vulnerabilities
Defending Apache Web Server
M'***zoft Internet Information Server (IIS)
IIS: Security Features
IIS: Attacking General Problems
IIS: IUSER or IWAM Level Access
IIS: Administrator or Sys Level Access
IIS: Clearing IIS Logs
IIS: Defending and Countermeasures
Web Server Vulnerability Scanners
Demo - Hacking Web Servers
Module 6 Review
Module 7
Hacking & Defending Web Applications
Background on Web Threat & Design
Basic Infrastructure Information
Information Leaks on Web Pages
Hacking over SSL
Use the Source, Luke…
Functional/Logic Testing
Attacking Authentication
Attacking Authorization
Debug Proxies: @stake webproxy
Input Validation Attacks
Attacking Session State
Attacking Web Clients
Cross-Site Scripting (XSS) Threats
Defending Web Applications
Module 7 Review
Module 8
Sniffers and Session Hijacking
Sniffers
Why Are Sniffers so Dangerous?
Collision & Broadcast Domains
VLANs and Layer-3 Segmentation
tcpdump & WinDump
Berkley Packet Filter (BPF)
Libpcap & WinPcap
BUTTSniffing Tool and dSniff
Ethereal
Mitigation of Sniffer Attacks
Antisniff
ARP Poisoning
MAC Flooding
DNS and IP Spoofing
Session Hijacking
Sequence Numbers
Hunt
Ettercap
Source Routing
Hijack Countermeasures
Demo - Sniffers
Module 8 Review
Module 9
Hacking & Defending Wind0wz Systems
Physical Attacks
LANMan Hashes and Weaknesses
WinNT Hash and Weaknesses
Look for Guest, Temp, Joe Accounts
Direct Password Attacks
Before You Crack: Enum Tool
Finding More Account Information
Cracking Passwords
Grabbing the SAM
Crack the Obtained SAM
LSA Secrets and Trusts
Using the Newly Guessed Password
Bruteforcing Other Services
Operating System Attacks
Hiding Tracks: Clearing Logs
Hardening Wind0wz Systems
Strong 3-Factor Authentication
Creating Strong Passwords
Authentication
Wind0wz Account Lockouts
Auditing Passwords
File Permissions
Demo - Attacking Wind0wz Systems
Module 9 Review
Module 10
Hacking & Defending Unix Systems
Physical Attacks on Linux
Password Cracking
Brute Force Password Attacks
Stack Operation
Race Condition Errors
Format String Errors
File System Attacks
Hiding Tracks
Single User Countermeasure
Strong Authentication
Single Sign-On Technologies
Account Lockouts
Shadow Password Files
Buffer Overflow Countermeasures
LPRng Countermeasures
Tight File Permissions
Hiding Tracks Countermeasures
Removing Unnecessary Applications
DoS Countermeasures
Hardening Scripts
Using SSH & VPNs to Prevent Sniffing
Demo - Attacking Unix Systems
Module 10 Review
Module 11
Rootkits, Backdoors, Trojans & Tunnels
Types Of Rootkits
A Look at LRK
Examples of Trojaned Files
Wind0wz NT Rootkits
NT Rootkit
AFX Wind0wz Rootkit 2003
Rootkit Prevention Unix
Rootkit Prevention Wind0wz
netcat
netcat: Useful Unix Commands
netcat: What it Looks Like
VNC-Virtual Network Computing
Backdoor Defenses
Trojans
Back Orifice 2000
NetBus
SubSeven
Defenses to Trojans
Tunneling
Loki
Other Tunnels
Q-2.4 by Mixter
Starting Up Malicious Code
Defenses Against Tunnels
Manually Deleting Logs
Tools to Modify Logs
Demo - Trojans
Module 11 Review
Module 12
Denial of Service and Botnets
Denial-of-Service Attacks
CPUHog
Ping of Death
Teardrop Attacks
Jolt2
Smurf Attacks
SYN Attacks
UDP Floods
Distributed DoS
DDoS Tool: Trin00
Other DDoS Variation
History of Botnets
Anatomy of a Botnet
Some Common Bots
Demo - Denial of Service
Module 12 Review
Module 13
Automated Pen Testing Tools
General: Definitions
General:What?
General: Why?
Core Impact™ Framework
Core Impact™ Operation
Canvas™ Framework
Canvas™ Operation
Metasploit Framework
Metasploit Operation
Demo - Automated Pen Testing
Module 13 Review
Module 14
Intrusion Detection Systems
Types of IDSs
Network IDSs
Distributed IDSs (DIDSs)
Anomaly Detection
Signature Detection
Common IDS Software Products
Introduction to Snort
Attacking an IDS
Eluding Techniques
Testing an IDS
Hacking Tool - NIDSbench
Hacking Tool - Fragroute
Hacking Tool - SideStep
Hacking Tool - ADMmutate
Other IDS Evasion Tools
Demo - IDS and Snort
Module 14 Review
Module 15
Firewalls
Firewall Types
Application Layer Gateways
ALGs (Proxies)
Stateful Inspection Engine
Hybrid Firewall
Host-Based Firewall
Network-Based Firewall
DMZ (Demilitarized Zone)
Back-to-Back Firewalls
Bastion Hosts
Control Traffic Flow
Multiple DMZs
Controlling Traffic Flow
Why Do I Need a Firewall?
What Should I Filter?
Egress Filtering
Network Address Translation (NAT)
Firewall Vulnerabilities
IPTables/NetFilter
Default Tables and Chains
iptables Syntax 1
iptables Syntax 2
Sample IPTables Script 1
Sample IPTables Script 2
Persistent Firewalls
Firewall Identification
Firewalk
Tunneling with Loki
Tunneling with NetCat/CryptCat
Port Redirection with Fpipe
Denial-of-Service Attacks Risk?
Demo - Firewalls and IP Tables
Module 15 Review
Module 16
Honeypots and Honeynets
What Is a Honeypot?
Advantages and Disadvantages
Types and Categories of Honeypots
Honeypot: Tarpits
Honeypot: Kfsensor
Honeypot: Honeyd
Sample Honeyd Configuration
High-Interaction Honeypot
Project HoneyNet
Types of Honeynets
The Main Difference is Data Control
GEN II Data Control: Honeywall CD
Gen II Data Capture: Sebek & Sebek II
Automated Alerting
Testing
Legal Issues
Demo - Setting up a Honeypot
Module 16 Review
Module 17
Ethics and Legal Issues
The Costs
Relation to Ethical Hacking?
The Dual Nature of Tools
Good Instead of Evil?
Recognizing Trouble When It Happens
Emulating the Attack
Security Does Not Like Complexity
Proper and Ethical Disclosure
CERT’s Current Process
Full Disclosure Policy
Organization for Internet Safety (OIS)
What Should We Do from Here?
Legal Meets Information Systems
Addressing Individual Laws
18 USC SECTION 1029
18 USC SECTION 1030
1030: Worms and Viruses
Blaster Worm Attacks
Civil vs. Criminal
18 USC SECTIONS 2510 and 2701
Digital Millennium Copyright Act
Cyber Security Enhancement Act
Module 17 Review
Course Closure
CD1.Ethical.Hacking.and.Penetration
Code:
http://rapidshare.com/files/24150271/Module_1.part01.rar
http://rapidshare.com/files/24150273/Module_1.part02.rar
http://rapidshare.com/files/24150275/Module_1.part03.rar
http://rapidshare.com/files/24150276/Module_1.part04.rar
http://rapidshare.com/files/24159635/Module_1.part05.rar
http://rapidshare.com/files/24159637/Module_1.part06.rar
http://rapidshare.com/files/24159638/Module_1.part07.rar
http://rapidshare.com/files/24159639/Module_1.part08.rar
http://rapidshare.com/files/24163957/Module_1.part09.rar
http://rapidshare.com/files/24163959/Module_1.part10.rar
CD2 Footprinting and Reconnaissance
Code:
http://rapidshare.com/files/24168655/Module_2.part01.rar
http://rapidshare.com/files/24168656/Module_2.part02.rar
http://rapidshare.com/files/24168657/Module_2.part03.rar
http://rapidshare.com/files/24168658/Module_2.part04.rar
http://rapidshare.com/files/24174114/Module_2.part05.rar
http://rapidshare.com/files/24174115/Module_2.part06.rar
http://rapidshare.com/files/24310589/Module_2.part07.rar
http://rapidshare.com/files/24310590/Module_2.part08.rar
http://rapidshare.com/files/24310591/Module_2.part09.rar
CD3 TCP/IP Basics and Scanning
Code:
http://rapidshare.com/files/24321107/mod.3.part1.rar
http://rapidshare.com/files/24321109/mod.3.part2.rar
http://rapidshare.com/files/24339724/mod.3.part3.rar
CD4 Enumeration and Verification
Code:
http://rapidshare.com/files/25291513/module.4.part1.rar
http://rapidshare.com/files/25291516/module.4.part2.rar
http://rapidshare.com/files/25297786/module.4.part3.rar
http://rapidshare.com/files/25297787/module.4.part4.rar
CD5 Hacking & Defending Wireless/Modems
Code:
http://rapidshare.com/files/24480780/module_5.part1.rar
http://rapidshare.com/files/24480781/module_5.part2.rar
http://rapidshare.com/files/24480784/module_5.part3.rar
http://rapidshare.com/files/24480785/module_5.part4.rar
http://rapidshare.com/files/24480786/module_5.part5.rar
http://rapidshare.com/files/24480787/module_5.part6.rar
CD6 Hacking & Defending Web Servers
Code:
http://rapidshare.com/files/28925031/Module.6.Hacking.Defending.Web.Servs.part01.rar
http://rapidshare.com/files/28925032/Module.6.Hacking.Defending.Web.Servs.part02.rar
http://rapidshare.com/files/28925034/Module.6.Hacking.Defending.Web.Servs.part03.rar
http://rapidshare.com/files/28925035/Module.6.Hacking.Defending.Web.Servs.part04.rar
http://rapidshare.com/files/28931012/Module.6.Hacking.Defending.Web.Servs.part05.rar
http://rapidshare.com/files/28931013/Module.6.Hacking.Defending.Web.Servs.part06.rar
CD7.Hacking.Defending.Web.Applications
Code:
http://rapidshare.com/files/26188740/Module.7.part1.rar
http://rapidshare.com/files/26188742/Module.7.part2.rar
http://rapidshare.com/files/26196529/Module.7.part3.rar
CD8. .Sniffers.and.Session.Hijacking
Code:
http://rapidshare.com/files/26196533/Module.8.part1.rar
http://rapidshare.com/files/26360406/Module.8.part2.rar
http://rapidshare.com/files/26360407/Module.8.part3.rar
CD9.Hacking.Defending.Wind0wz.Systems
Code:
http://rapidshare.com/files/26370153/Module.9.part1.rar
http://rapidshare.com/files/26376136/Module.9.part2.rar
http://rapidshare.com/files/26370156/Module.9.part3.rar
CD10.Hacking.Defending.Unix.Systems
Code:
http://rapidshare.com/files/28216732/Module_10.part01.rar
http://rapidshare.com/files/28216733/Module_10.part02.rar
http://rapidshare.com/files/28216734/Module_10.part03.rar
http://rapidshare.com/files/28216735/Module_10.part04.rar
http://rapidshare.com/files/28216737/Module_10.part05.rar
http://rapidshare.com/files/28216740/Module_10.part06.rar
http://rapidshare.com/files/28222043/Module_10.part07.rar
http://rapidshare.com/files/28222044/Module_10.part08.rar
http://rapidshare.com/files/28222045/Module_10.part09.rar
http://rapidshare.com/files/28222046/Module_10.part10.rar
CD .11.Rootkits.Backdoors.Trojans.Tunnels
Code:
http://rapidshare.com/files/28236225/Module_11.part01.rar
http://rapidshare.com/files/28236226/Module_11.part02.rar
http://rapidshare.com/files/28236228/Module_11.part03.rar
http://rapidshare.com/files/28236229/Module_11.part04.rar
http://rapidshare.com/files/28236231/Module_11.part05.rar
http://rapidshare.com/files/28236233/Module_11.part06.rar
http://rapidshare.com/files/28238956/Module_11.part07.rar
http://rapidshare.com/files/28238959/Module_11.part08.rar
CD.12.Denial.of.Service.and.Botnets
Code:
http://rapidshare.com/files/28250428/Module_12.part1.rar
http://rapidshare.com/files/28250430/Module_12.part2.rar
http://rapidshare.com/files/28250431/Module_12.part3.rar
http://rapidshare.com/files/28250432/Module_12.part4.rar
http://rapidshare.com/files/28250433/Module_12.part5.rar
http://rapidshare.com/files/28250434/Module_12.part6.rar
http://rapidshare.com/files/28250435/Module_12.part7.rar
CD.13..Automated.Pen.Testing.Tools
Code:
http://rapidshare.com/files/28259605/Module.13.part01.rar
http://rapidshare.com/files/28259607/Module.13.part02.rar
http://rapidshare.com/files/28259608/Module.13.part03.rar
http://rapidshare.com/files/28259610/Module.13.part04.rar
http://rapidshare.com/files/28259612/Module.13.part05.rar
http://rapidshare.com/files/28259613/Module.13.part06.rar
http://rapidshare.com/files/28259614/Module.13.part07.rar
CD.14.Intrusion.Detection.Systems
Code:
http://rapidshare.com/files/28268932/Module_14.part01.rar
http://rapidshare.com/files/28268933/Module_14.part02.rar
http://rapidshare.com/files/28268935/Module_14.part03.rar
http://rapidshare.com/files/28268936/Module_14.part04.rar
http://rapidshare.com/files/28268937/Module_14.part05.rar
http://rapidshare.com/files/28268938/Module_14.part06.rar
http://rapidshare.com/files/28275713/Module_14.part07.rar
http://rapidshare.com/files/28275714/Module_14.part08.rar
http://rapidshare.com/files/28275715/Module_14.part09.rar
http://rapidshare.com/files/28275716/Module_14.part10.rar
CD .15.Firewalls
Code:
http://rapidshare.com/files/28283458/Module_15.part01.rar
http://rapidshare.com/files/28283459/Module_15.part02.rar
http://rapidshare.com/files/28283460/Module_15.part03.rar
http://rapidshare.com/files/28283461/Module_15.part04.rar
http://rapidshare.com/files/28283464/Module_15.part05.rar
http://rapidshare.com/files/28283465/Module_15.part06.rar
http://rapidshare.com/files/28338024/Module_15.part07.rar
http://rapidshare.com/files/28338028/Module_15.part08.rar
http://rapidshare.com/files/28338029/Module_15.part09.rar
http://rapidshare.com/files/28338030/Module_15.part10.rar
http://rapidshare.com/files/28338032/Module_15.part11.rar
CD. 16.Honeypots.and.Honeynets
Code:
http://rapidshare.com/files/28345006/Module_16.part01.rar
http://rapidshare.com/files/28345007/Module_16.part02.rar
http://rapidshare.com/files/28345008/Module_16.part03.rar
http://rapidshare.com/files/28345009/Module_16.part04.rar
http://rapidshare.com/files/28345010/Module_16.part05.rar
http://rapidshare.com/files/28345011/Module_16.part06.rar
http://rapidshare.com/files/28354433/Module_16.part07.rar
http://rapidshare.com/files/28354435/Module_16.part08.rar
CD. 17 .Ethics.and.Legal.Issues
Code:
http://rapidshare.com/files/28354436/Module_17.part1.rar
http://rapidshare.com/files/28354437/Module_17.part2.rar
http://rapidshare.com/files/28354438/Module_17.part3.rar
http://rapidshare.com/files/28354439/Module_17.part4.rar
http://rapidshare.com/files/28357536/Module_17.part5.rar
http://rapidshare.com/files/28357537/Module_17.part6.rar
PASS included in rar file description
Tuesday, February 5, 2008
Disable yahoo from tracking you
As you all know, Yahoo! upgraded its features and the capacities of the mail accounts have grown to 2GB. That's good for sure, but the "monitoring" methods that we all have been far too familiar with in the last couple of years have been renewed with this move also. Yahoo! is now keeping track of which sites its members that are getting into groups or using Yahoo! services are visiting and storing this data with a method called "Web Beacons". The aim is to give these statistics to the partner companies arranged by agreement and to improve the "advertisement guiding" function.
However, those who are bothered by this and do not want to be kept track of have still a choice. Yahoo! has hidden this option way deep inside somewhere but I'm declaring it here in case there are people who want it anyway:
1. Go to the address
CODE http://privacy.yahoo.com/privacy
and click the "Cookies" link under the "Special Topics" column.
2. Click the "Web Beacons" link under the "Reference Links" Column.
3. On this page, click the "click here to opt out" link toward the end of the third paragraph under the "Outside the Yahoo! Network" title.
4. After a while, a page that says you have been out of the monitoring program will load. Without doing anything, close that page or continue your usual surfing by typing another address in the address bar. (Do NOT click the "Cancel Opt-out" button, your action will be cancelled!)
However, those who are bothered by this and do not want to be kept track of have still a choice. Yahoo! has hidden this option way deep inside somewhere but I'm declaring it here in case there are people who want it anyway:
1. Go to the address
CODE http://privacy.yahoo.com/privacy
and click the "Cookies" link under the "Special Topics" column.
2. Click the "Web Beacons" link under the "Reference Links" Column.
3. On this page, click the "click here to opt out" link toward the end of the third paragraph under the "Outside the Yahoo! Network" title.
4. After a while, a page that says you have been out of the monitoring program will load. Without doing anything, close that page or continue your usual surfing by typing another address in the address bar. (Do NOT click the "Cancel Opt-out" button, your action will be cancelled!)
Sunday, February 3, 2008
Top 6 freewares for your computer
1.OpenOfficeOrg -Alternate to Microsoft Office.Has all the features of Microsoft Office and it is free.
Download
2.VLC Media Player - It has the capacity to play any type of media (popular ones), including Flash Videos (flv) and Windows Media Videos. It’s very light and thus ideal for all purposes.
Download
3.Mozilla Firefox- This is one of the best and the most popular browser, it is light, now it is very secure and proxy configuration is very easy. It also has a script executing add on called Greasemonkey which is very helpful. There are many other addons for Mozilla.
Download
4.Opera Browser- A SuperFast Browser that is secure and Free. My Favoruite Browser with Awesome unique features
Download
5.Gimp - It’s a free image editor tool. Numerous digital photo imperfections can be easily compensated for using GIMP. Fix perspective distortion caused by lens tilt simply choosing the corrective mode in the transform tools. Eliminate lens barrel distortion and vignetting with a powerful filter but a simple interface.
Download
6.AVG - This company claims that it has provided security for over 50 million computers, it is a good anti-virus solution. It can protect you from spywares, trojans, worms, virus, filters junk emails and more.
Download
Download
2.VLC Media Player - It has the capacity to play any type of media (popular ones), including Flash Videos (flv) and Windows Media Videos. It’s very light and thus ideal for all purposes.
Download
3.Mozilla Firefox- This is one of the best and the most popular browser, it is light, now it is very secure and proxy configuration is very easy. It also has a script executing add on called Greasemonkey which is very helpful. There are many other addons for Mozilla.
Download
4.Opera Browser- A SuperFast Browser that is secure and Free. My Favoruite Browser with Awesome unique features
Download
5.Gimp - It’s a free image editor tool. Numerous digital photo imperfections can be easily compensated for using GIMP. Fix perspective distortion caused by lens tilt simply choosing the corrective mode in the transform tools. Eliminate lens barrel distortion and vignetting with a powerful filter but a simple interface.
Download
6.AVG - This company claims that it has provided security for over 50 million computers, it is a good anti-virus solution. It can protect you from spywares, trojans, worms, virus, filters junk emails and more.
Download
Subscribe to:
Posts (Atom)


